Leaving software unpatched is one of the most basic, unforced errors an executive can make, but companies large and small keep learning this the hard way.
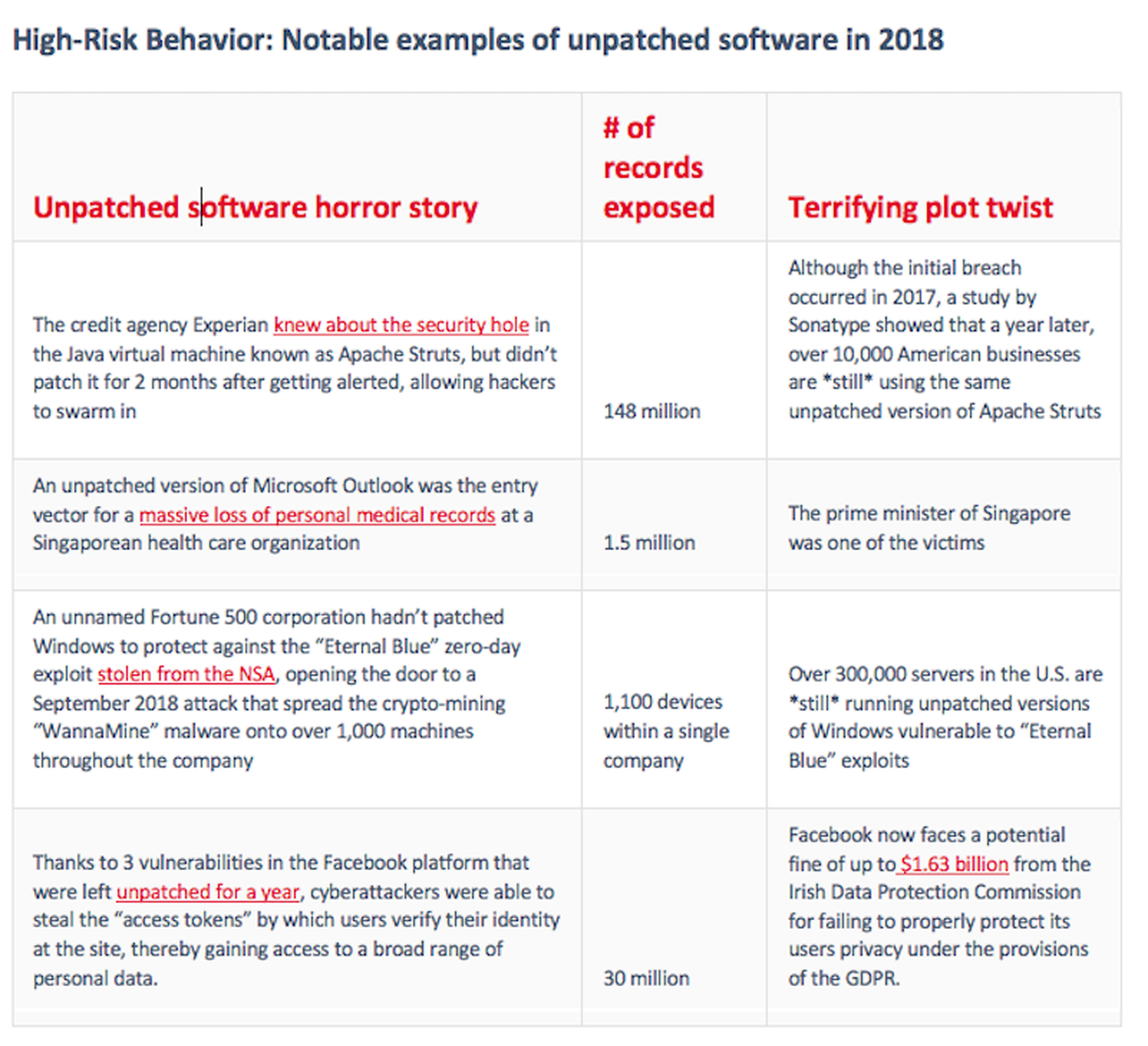
Consider that last year, a vulnerability in a Java virtual machine that the credit agency Experian failed to update for two months allowed hackers to access over 145 million credit reports, wiping out more than $5 billion in market cap and costing the CEO his job. A single unpatched copy of Microsoft Outlook led to the July 2018 compromise of 1.5 million health records, including that of the prime minister of Singapore. Meanwhile, at an unnamed Fortune 500 corporation in September 2018, an outdated version of Windows opened the door to a crypto-mining attack that quickly moved to over 1,100 machines throughout the company.

These are only the most colorful recent examples of negligent patching practices, but many executives have their heads in the sand about the severity of the problem. A survey by the Ponemon Institute showed that nearly 60% of breaches over the past two years were attributable to unpatched software — and 34% of companies knew about the vulnerability in advance of the attack and simply hadn’t gotten around to dealing with the problem. Almost all small businesses would be better off assigning a security-savvy IT professional to handle patching, but a recent study by Insureon showed that 61% of small business owners handle IT themselves, and 84% don’t think they are at a risk of an attack. All this in spite of the fact that 58% of cyber attacks target small businesses.
“Small business owners tend not to focus on security because they see it as a liability and a cost center,” says AJ Singh, vice-president of product at NinjaRMM. “They don’t consider the losses from outages.”
And the cost of a breach is considerable, averaging about $120,000 for small and medium-sized businesses, according to Kaspersky. An even more alarming statistic is that half of small businesses hit by a successful cyber attack go out of business within 6 months, according to an estimate from the National Cybersecurity Alliance.
But even when execs are aware of the importance of patching, the sheer volume of needed fixes and the high error rate mean that not every company stays protected. Keeping software up-to-date is harder than it seems.
What is unpatched software?
Unpatched software refers to computer code with known security weaknesses. Once the vulnerabilities come to light, software vendors write additions to the code known as “patches” to cover up the security “holes.” Running unpatched software is a risky activity because by the time a patch emerges, the criminal underground is typically well-aware of the vulnerabilities.
What else goes wrong?
Though reputable vendors typically offer free, automated patching for outdated software, the process can sometimes break down or cause software to malfunction. Our internal research at NinjaRMM shows that 25-30% of Windows 10 patches fail, which is why we custom-built a utility to successfully execute the process.
Also, the ever-changing nature of cyber attacks means that most busy executives don’t have the time to keep up with every needed fix. For example, Webroot found that 93% of malware detected in 2017 occurred on only one machine — in other words, most malware morphs into a novel form that traditional antivirus signature databases can’t recognize.
“Patching is an uphill battle,” Singh says. “There are new threats out every day.”
Ultimately, patching is both too important and too tedious for non-professionals to manage. And frankly, it can be a headache for MSPs too. That’s why NinjaRMM designed a patch management system that takes the pain out of this essential process. MSP managers have the option to “set it and forget it,” meaning they can issue a blanket instruction to update O.S. and third-party software across all devices. Or they can tweak patching at a granular level, electing to manipulate settings on a per-device or per-group basis.
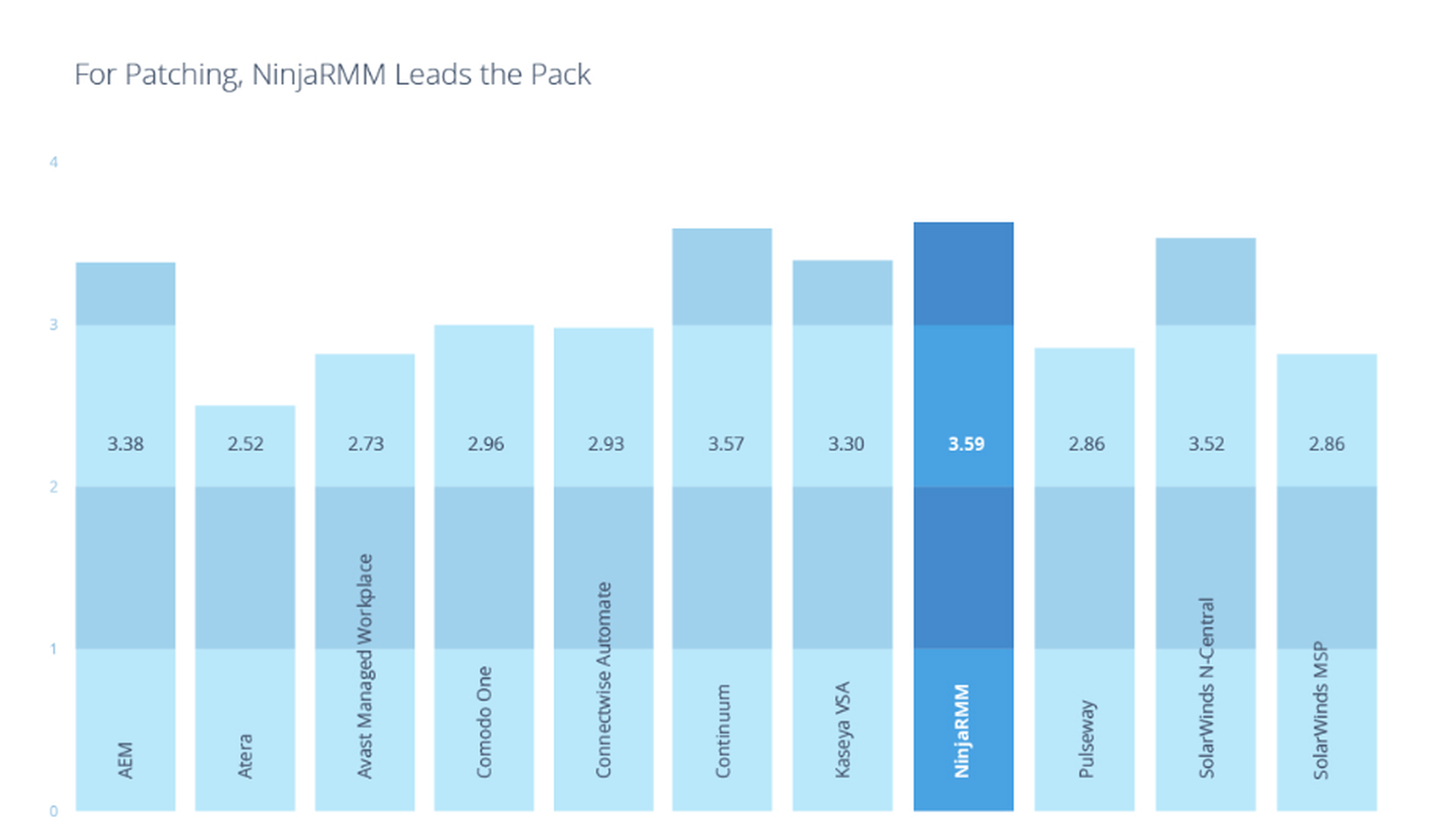
And you don’t have to take our word for it. An independent survey of MSP users recently rated NinjaRMM as having the top software patching functionality among its competitors in the remote monitoring and management (RMM) tool space.
To see NinjaRMM in action, sign-up for a free trial.
Andrew Rosenblum is the Community Manager at NinjaRMM. Read more NinjaRMM blogs here.




