
The year is young, but 2019 is already shaping up to be another rough one on the security front. Particularly concerning is the growing number of attacks explicitly targeting MSPs and their customers.
In case you haven’t been keeping score at home let’s review some of the biggest active threats and dive into what you can be doing to better protect yourself. If you’re more interested in going straight to the tips you can download our new 2019 MSP Cybersecurity Checklist here.

Attacks targeting MSPs are on the rise: 3 big threats to be aware of
1) China-based hacking group APT10
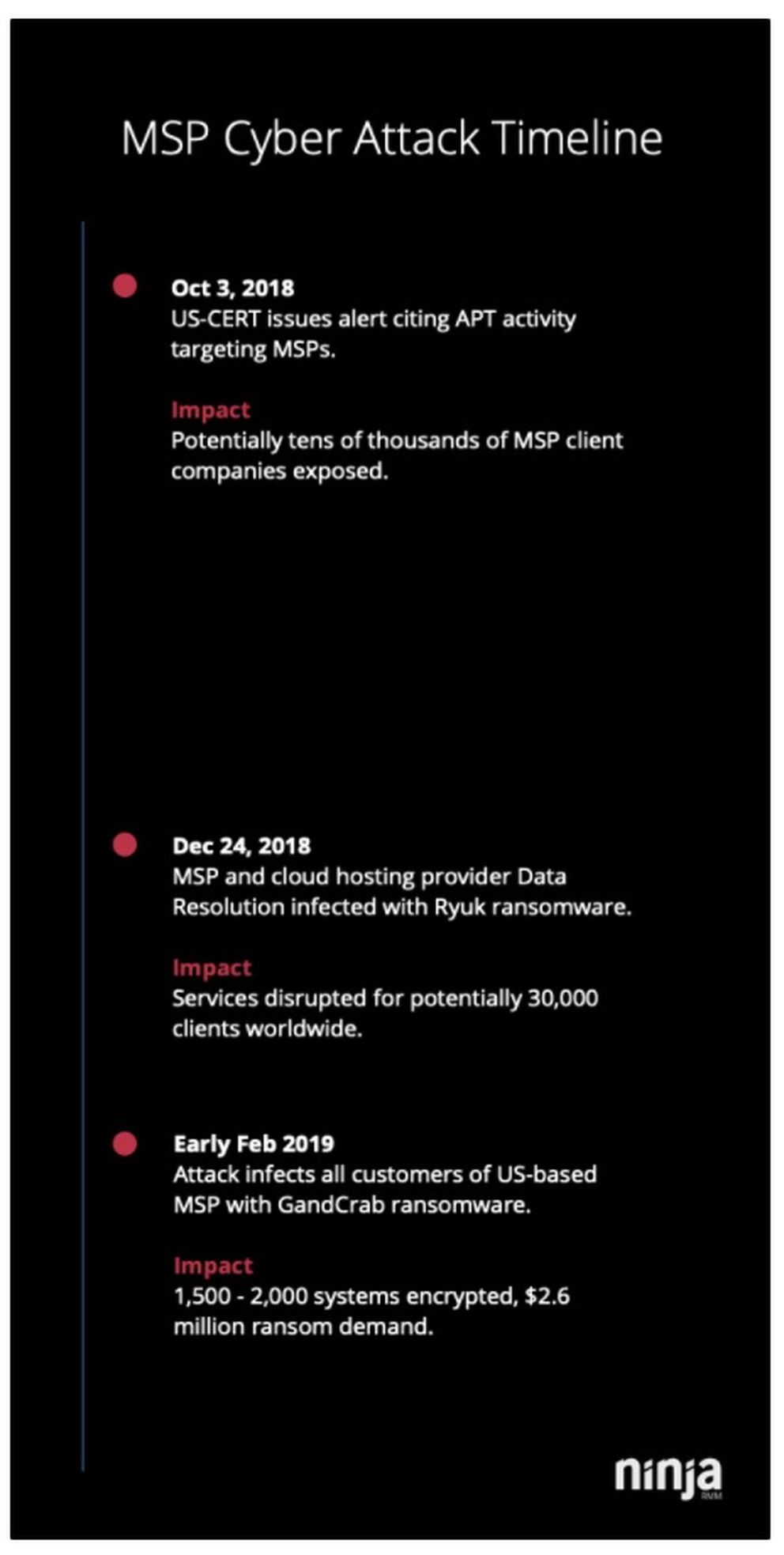
In October, the United States Computer Emergency Readiness Team (US-CERT) issued an alert acknowledging a sustained and wide-ranging effort by advanced persistent threat (APT) actors to infiltrate MSPs and their customers. It’s believed the campaign, referred to as Operation Cloud Hopper, has been active since 2016, and has resulted in attackers gaining unprecedented access to MSP customer networks.
Two of the larger MSP victims were later identified as Hewlett Packard Enterprise (HPE) and IBM, though officials have warned that’s only the tip of the iceberg. Alastair MacGibbon, head of Australia’s Cyber Security Centre, described the operation as “the biggest and most audacious campaign I’ve ever seen… massive in its scope and its scale.” He expressed concern that tens of thousands of companies may have been exposed via their MSPs.
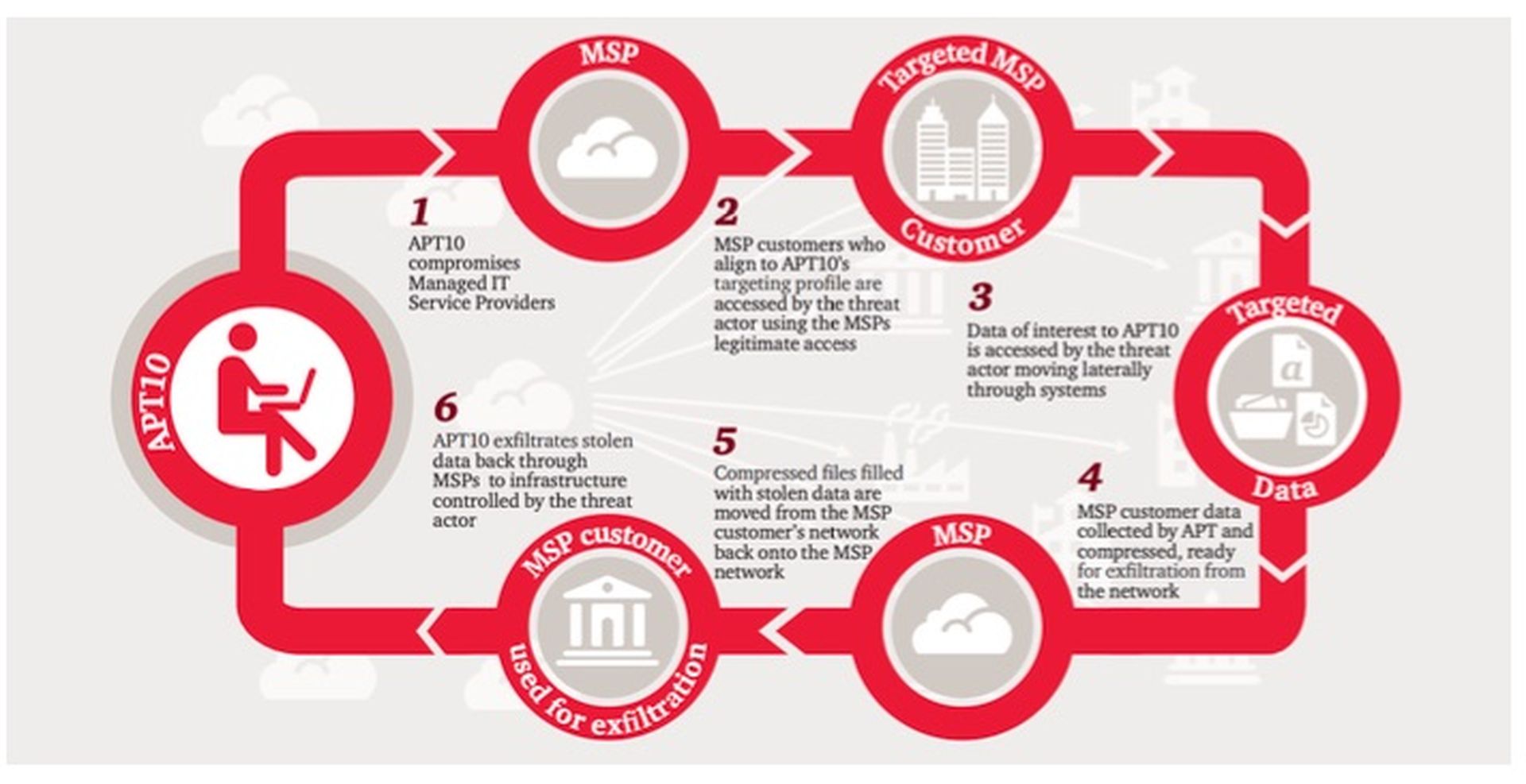
Cloud Hopper attack diagram (PwC)
Key facts
- Attackers gain initial access to MSPs via spear phishing emails
- They then spread to MSP customer networks by abusing legitimate, harvested MSP credentials and remote access tools like RDP
- They evade detection by using legitimate, built-in administration tools like PowerShell, Robocopy, and PuTTY to exfiltrate data and conduct other malicious activities
- Attackers gain persistence on compromised machines by using scheduled tasks or Windows services
- The primary goal of the campaign appears to be espionage and intellectual property theft
2) Ryuk ransomware
Attacks involving Ryuk differ from other ransomware infections in several key ways. First, they are typically preceded by Emotet or Trickbot — trojans that establish footholds across victim networks and lay the groundwork for attackers identifying and encrypting the most critical assets. Attackers have waited days, weeks, or even months to deploy Ryuk, taking time to scout out the network, disable security and backups, and plan the deployment of the ransomware to happen overnight, on the weekend, or on a holiday in order to maximize damage before victims can respond.
That’s exactly what happened to Data Resolution, a California-based MSP and cloud hosting provider that found itself grappling with a Ryuk ransomware infection this past Christmas Eve. Locked out of its systems, the company was forced to shut down the network and scramble to hire security consultants available to work on Christmas Day. Then there was the matter of notifying Data Resolution’s 30,000 customers why many may have lost access to their email and databases.
While the ransom amount was not disclosed, previous Ryuk demands have typically been in the six-figures. All told, it’s estimated this selective, targeted strategy has generated nearly $4 million for the criminals behind Ryuk in just six months. But if you’re thinking Ryuk is only a threat to large MSPs, think again. Victims have also included a small North Carolina water utilityand the city of Valdez, Alaska (population 3,862). It’s not strictly about size, it’s about leverage. If attackers determine you’re an MSP who provides critical services to clients they may be only too motivated to see how eager you are to avoid client-facing damage and downtime.
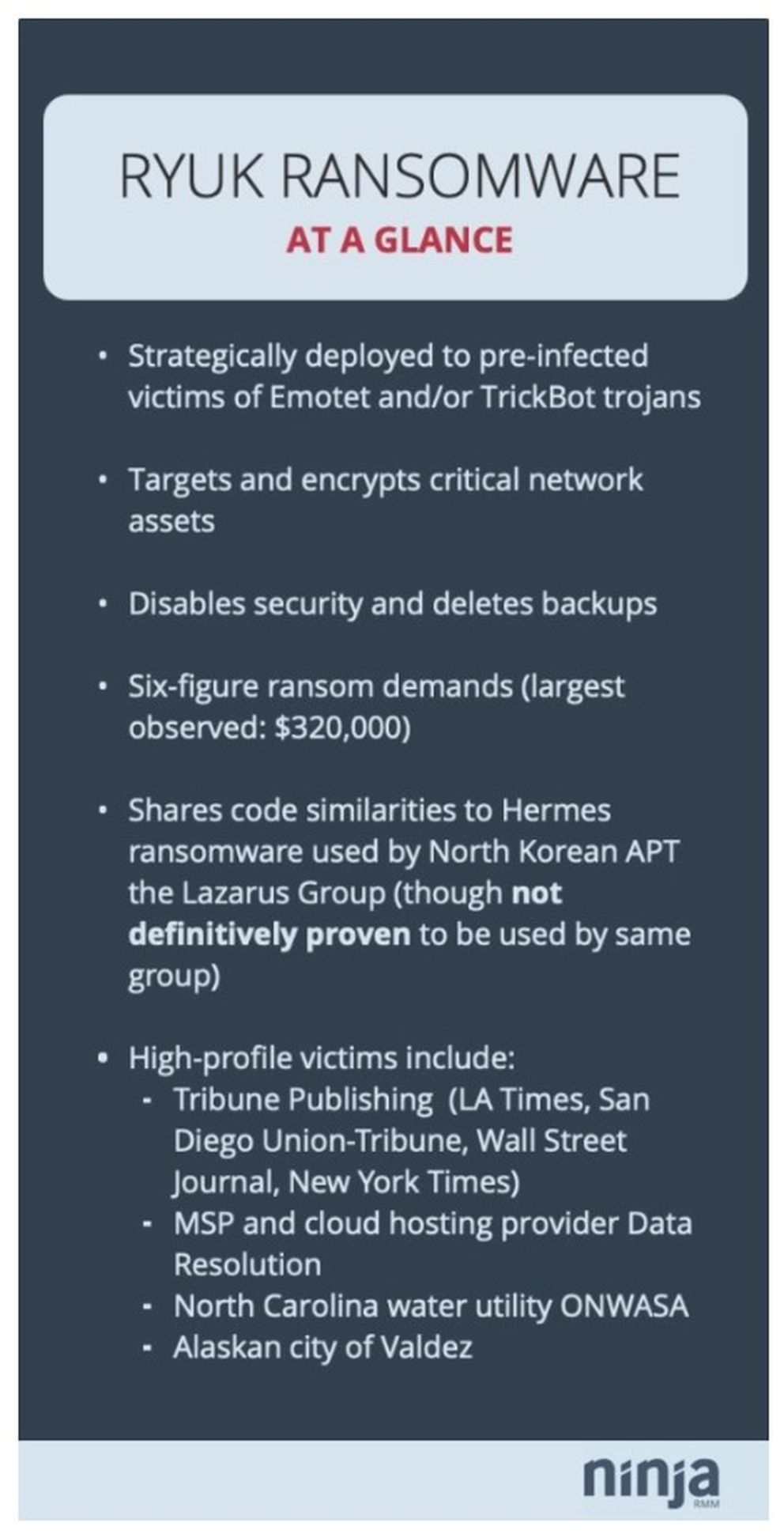
Ryuk ransomware key facts
- Ryuk is selectively deployed to victims infected with Emotet and/or TrickBot (which are typically delivered via malicious emails)
- Prior to deployment, attackers conduct network reconnaissance by using standard Windows command-line tools to avoid detection
- They achieve lateral movement throughout victim networks by abusing legitimate, harvested credentials and remote access tools like RDP
- To maintain access, they create service user accounts that can also be used to react to recovery efforts
- Once they gain access to accounts with elevated privileges they disable/remove security software, logging, and backups
- They use batch scripts and Windows tools like PsExec to deploy Ryuk across individual machines
3) GandCrab ransomware
Currently the most prolific ransomware variant in terms of sheer volume of infections, GandCrab was recently used to make a MSP’s worst nightmare come true. As detailed on Reddit, in early February a mid-size MSP saw all of their 80 clients infected with ransomware. With an estimated 1,500 to 2,000 client systems were encrypted, the MSP faced a ransom demand of $2.6 million.
As if that wasn’t bad enough, attackers had utilized the MSP’s own RMM tool to deploy the ransomware, making them directly responsible.
The source of the problem was an outdated ConnectWise ManagedITSync integration plugin for Kaseya VSA. Details regarding a vulnerability in the integration had been disclosed along with a PoC in November 2017, but in this case updates resolving the issue had not been applied or applied correctly.
As a result, attackers were able to gain administrative access to the MSP’s Kaseya RMM tool and use it to deploy GandCrab to every endpoint under the MSP’s management.
According to Kyle Hanslovan of Huntress Labs, this particular MSP unfortunately wasn’t alone. At least four other MSPs also suffered similar fates, with “all of their clients’ endpoints encrypted with GandCrab in a single swoop.”
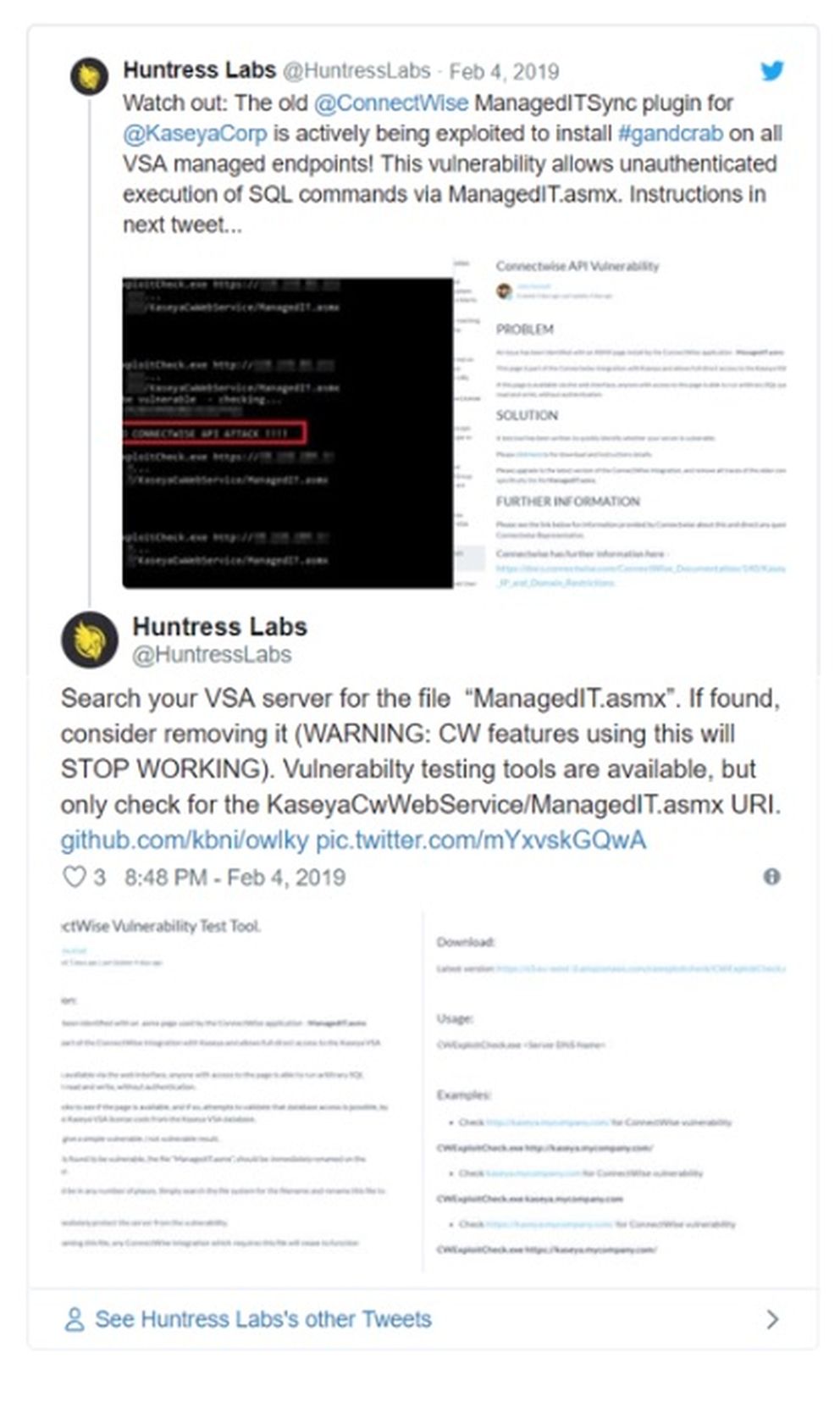
Huntress Labs shared a warning and instructions for Kaseya VSA users to confirm whether they’re vulnerable (see image).
GandCrab decryptor tool available: The good news is victims of GandCrab may be able to decrypt and recover their encrypted data without paying the ransom. That’s because researchers at Bitdefender have released an update to their free GandCrab decryption tool. The tool works on files encrypted by GandCrab between November 2018 and February 2019. It should be noted, however, that Bitdefender has released decryption tools before, and the bad guys behind GandCrab have released updated versions of the ransomware that make them ineffective, typically within days.
The targeted nature of the attack and the high ransom amount is a departure for GandCrab actors. Up to this point, they had largely been observed deploying the ransomware via exploit kits and indiscriminate spam campaigns. It’s another sign that the shift to coordinated, targeted attacks is a dangerous and growing trend.
Why are MSPs being targeted by cyber criminals?
In a word: access. MSPs serve numerous clients who entrust them with the keys to their kingdoms. MSP infrastructures are designed to provide technicians with easy direct access to those clients so they can hop on and off to troubleshoot, perform maintenance, deploy software, etc. It’s easy to understand why cyber criminals find those capabilities incredibly appealing. Compromise just one MSP and they can find themselves with access to a score of potential victims.
In addition, because the core offering MSPs provide is keeping their client networks secure and running smoothly, the threat of client-facing disruption and damage makes MSPs prime extortion targets. If you woke up one morning to find all of your clients had been infected with ransomware how much would you be willing to pay to make the problem go away? Paying ransoms is never advisable (nor simple nor a sure thing), but you can see why attackers may believe infecting MSPs and their customers gives them even more leverage than usual.
Finally, like many of the businesses they serve, MSPs are often small operations with limited staff and resources. While they have more knowledge and tools at their disposal, they still often lack dedicated security personnel (not to mention hours in the day to make absolutely sure they’re covering all their bases). As a result, they make softer targets than major corporations many times their size, but can still offer attackers potential access to just as many endpoints via their clients.
What happens when MSPs are compromised?
The stakes are high. Attackers are increasingly leveraging initial access to MSPs to gain access to their customers. As the recent wave of GandCrab attacks shows, the very tools and capabilities that make it possible for MSPs to serve their customers can be used against them. When that happens it can irreparably erode the trust at the heart of any MSP-client relationship.
No trust. No business.
5 keys to protecting your MSP business against this surge in targeted attacks
Securing your business isn’t a one-time activity, but there are concrete things you can do now to make it much more difficult for attackers to land and expand in your network. We’ll cover some of the more pressing items below, but you should also see our 2019 MSP Cybersecurity Checklist.
1) Restrict access across your network
Each of the attacks described above made use of legitimate privileges that can often be better locked down. The best way to do that is by establishing barriers between your users and assets. Start by taking a tiered approach to privileged access and adhering to the principle of least privilege — always limit privileges to the bare minimum required to get the job done.
Avoid sharing or reusing login credentials, and use a password manager to create strong, unique passwords. Enable multi-factor authentication whenever possible.
But don’t stop there. Make sure you’re using unique local admin passwords (Microsoft’s LAPS can help), and that you’ve removed end users from the local admin group. Don’t admin accounts unless it’s specifically necessary.
Also important: Lock down your systems to block lateral movement across workstations.
2) Secure your RMM and other remote access tools
Each of these tools should come with a reminder that says, “With great power comes great responsibility.” At a minimum, you should make sure you have MFA enabled and that you’re keeping these tools up-to-date. Yes, patching can be difficult, but these need to be a priority.
In addition, limit users who have access to these tools — and what they have access to within them — to the bare minimum necessary for them to do their jobs. In an ideal scenario, you should have logging enabled and be able to see who has accessed what, when.
And for the love of all that is holy, secure RDP.
3) Protect your users and lock down their endpoints
For as much as the threat landscape is changing, the vast majority of cyber attacks still start off the same way — with a user getting fooled by a malicious email. Protect your employees with email and web filtering tools that can help prevent them from making mistakes. If you haven’t already, it’s a good idea to set up DMARC, SPF, and DKIM, too.
In addition, take time to disable or restrict built-in Windows tools and functionality that attackers love to abuse. Restricting PowerShell should be at the top of the list, but you should also adjust endpoint settings to restrict the launch of script files, disable/restrict macros and OLE in Microsoft Office, and block a variety of programs like certutil, mshta, and regsvr32 from making outbound requests.
4) Actively monitor your own network for signs of compromise
RMM tools make monitoring your clients’ networks easy, but you should be keeping a close eye on your own network, as well. In the attack situations described above, alerts notifying the MSP of key events like new service installation, scheduled task creation, and registry changes may have been able to provide victims with critical early warning signs.
We’ve worked to make establishing these types of alerts easy thanks to the out-of-the-box alert templates in NinjaRMM.
5) Have an incident response plan ready
When a security incident does occur (it’s unfortunately a matter of when, not if) you need to be able to act quickly under pressure. That takes clear guidelines and effective planning. Take time to sit down with your team and work those things out. Establish roles and responsibilities. Have a plan for communicating — internally, with customers, authorities, and the public (if necessary). Research firms that specialize in incident response and have one on call should you ever need to escalate things quickly.
Finally, don’t just have a plan, test it. Run fire drills so you can uncover blindspots and things you should do differently. There will definitely be something.
Next (baby) steps
Taking all these suggestions in at once can make things seem too difficult. Who has time for any of this stuff, anyway? The key thing to remember is that you don’t need to do everything at once. You just need to do something. Progress can be gradual. Focus on one thing at a time. Keep in mind any improvements you can make now will be worthwhile and far less time-consuming/expensive than dealing with an active attack.
The alternative — doing nothing — is easy now, but disastrous in the long run. You can only dodge the bullet for so long. As these attacks show, the risk is only mounting.
To help you get started, download our new checklist packed with practical tips and links to free resources.

Jonathan Crowe is senior content manager at NinjaRMM. Read more NinjaRMM blogs here.




