In alignment with its mission to implement a Zero Trust security model across its products, services and entire partner ecosystem, Microsoft is putting an end to delegated admin privileges (DAP) in favour of more secure granular delegated admin privileges (GDAP). Admin privileges are essentially security measures that detail accesses between Microsoft partners—whether they’re indirect providers, indirect resellers or direct bill partners—and their clients. In other words, they affect how Microsoft partners interact with customer workloads in Microsoft 365, Dynamics 365 and Microsoft Azure. These changes therefore have an impact on any partners who transact in Microsoft’s CSP program.
Beginning May 22, 2023, Microsoft will transition both active and inactive DAP relationships to GDAP ones with limited Azure Active Directory (AAD) roles. Once this transition takes place, Microsoft will then remove corresponding DAP relationships 30 days later. Relationships that have already been transitioned from DAP to GDAP by Microsoft partners prior to May will not be affected, however Microsoft will officially disable any remaining DAP access by the end of July.
While increased security is undoubtedly a good thing, it’s understandable that many partners and their clients have questions about the move from DAP to GDAP, how it will affect them and how to transition clients themselves prior to Microsoft taking action.
What are granular delegated admin privileges (GDAP)?
Keeping with the Zero Trust principle of explicit verification and using least privileged access, GDAP provides more explicit roles and time-bound parameters for partner access to customer environments than DAP. They restrict access to customer tenants on a deeper level, thereby reducing security risk between Microsoft partners and their clients. More specifically, GDAP details access at the customer, partner tenant, partner user and workload levels for different Microsoft services.
The point of GDAP is ultimately to protect access to customer data. GDAP also helps partners accommodate clients with regulatory requirements to allow only least privileged access to providers.
How does GDAP work?
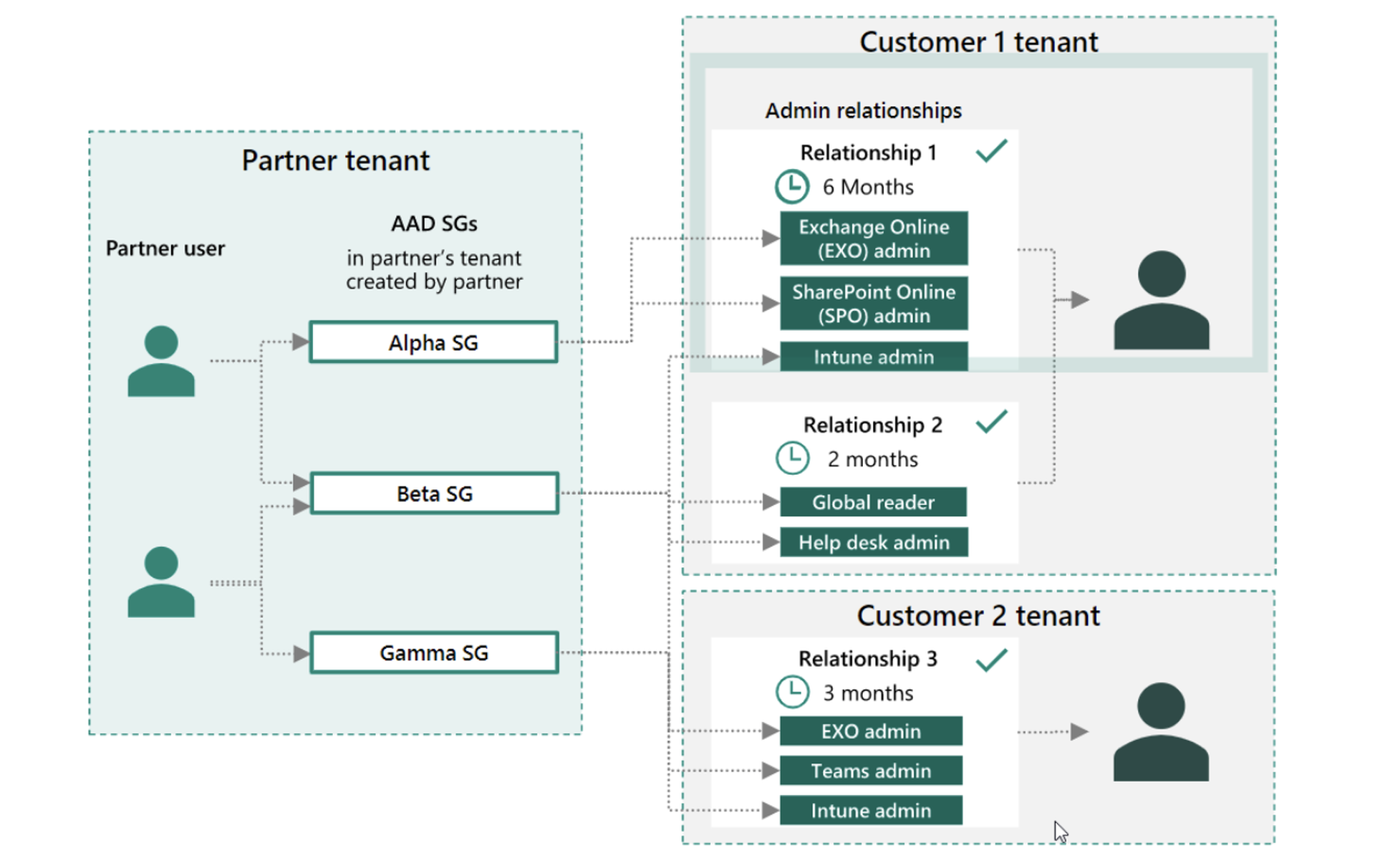
Once enabled, Microsoft partners can assign their users to different security groups and associated roles. These security groups are then given access to customer workloads for a fixed duration of time, up to a maximum of two years. Afterwards, the access automatically expires.
Security groups are created in partner tenants using Azure Active Directory (AAD). Some examples of different admin privileges include:
- Exchange Online admin
- SharePoint Online admin
- Intune admin
- Help desk admin
- Teams admin
Source: Microsoft
Transitioning from DAP to GDAP
At some point, Microsoft will stop creating new DAP relationships between providers, resellers and end-clients, and start removing inactive ones. This will turn off partners’ ability to manage various capabilities for customer tenants, such as creating support tickets for Microsoft on customers’ behalf. any existing Microsoft discounts they currently have with Sherweb will not be affected.
Nevertheless, partners, providers and resellers are strongly encouraged to start transitioning tenants from DAP to GDAP as soon as possible. To begin the transition, Microsoft has shared a number of steps for partners in the CSP program to follow.
Audit your existing DAP connections
To begin the move to GDAP, partners should first determine how users within their organization currently access customer tenants. This can be done using the DAP monitoring report in the Microsoft Partner Center. The report can also be used to remove inactive DAP connections. To access it, navigate to Partner Center, Account settings, Security center, and then Administrative relationships.

Source: Microsoft
Remove inactive DAP connections
Next, partners can go about removing DAP relationships. Make sure you notify customers before doing so, as users within your organization won’t be able to access customers’ online services once the connection is removed.
Start planning your transition
Before establishing GDAP connections with all your tenants, a certain degree of planning is advised. Think about what activities different people within your organization execute for customers to help figure out what kind of role they should have. As an example, here are some recommended roles for indirect providers and resellers to assign in order to transact and manage clients:
- New customer tenant creation
- Reseller relationship setup
- Purchase
- Subscription management
- Upgrades
- Conversions
- Customer user creation and license assignment
- Customer service requests
Initiate the move to GDAP
Once you have an idea of what roles you want to assign for your customers, it’s time to start the transition. Please note that this process will require customers to approve your request for a GDAP connection, so communicating with tenants about this change beforehand is probably a good idea. However, if you use Microsoft’s GDAP bulk migration tool Partners can use Microsoft 365 Lighthouse to complete the transition as well.

Source: Microsoft
Disable DAP for good
After completing the transition to GDAP, it’s recommended that partners disable DAP connections. This is done using the same DAP monitoring report in the Partner Center. Simply select the customer you want to turn off DAP for, then select Disable DAP.
How to create GDAP relationships with new customers
For new customer organizations, partners can adhere to the following steps for establishing GDAP relationships.
- In Microsoft’s Partner Center, select Customers, followed by a specific customer.
- Select Admin relationships, followed by Request admin relationship.
- Enter relevant details for the Admin relationship name and Duration.
- Select specific AAD roles, keeping in mind that least-privileged roles are recommended.
- Select Save for the selected roles.
- Selected roles will then appear in the Requested AAD roles section.
- Select Finalize request, which will then prompt an email send to the customer.
- Review your message to the affected customer with the GDAP invitation link.
- Send the email.
- You’re done!
What happens when GDAP connections expire
Whereas DAP connections had no expiration after a certain amount of time, GDAP connections do automatically in order to facilitate a more secure environment. When a GDAP relationship is about to expire, both the partner and customer will receive a notification by email 30 days, seven days and one day prior. Afterwards, partner users who were assigned to a security group for that customer will no longer have access or be able to administer services. To renew the duration of access permission, a new GDAP request will have to be sent to the customer.
Making sure you and your clients are ready for the DAP to GDAP transition
Microsoft partners should be advised that some dates regarding this transition are still in flux. These include when DAP relationships will stop being issued for newly created customer tenants, when default GDAP accesses for newly created tenants will be granted, and when the bulk migration tool for transitioning large numbers of clients from DAP to GDAP will be retired.
Understandably, staying on top of these updates can be challenging. Working with an expert provider that’s familiar with navigating the Microsoft ecosystem can help! Sherweb experts are well-versed in helping manage developments such as these that affect their business. Check out our Partner Guide to learn more about how Sherweb can help your business grow, or sign up for our partner program to get started today.
This guest blog is courtesy of Sherweb. Read more Sherweb guest blogs here. Regularly contributed guest blogs are part of ChannelE2E’s sponsorship program.




