Implementing robust security defense strategies helps mitigate the risk of cyberthreats in the early stages of an attack. Threat hunting is a key part of this strategy, enabling it to block unknown threats that slip through security controls and lurk in their organizations’ networks.

However, effective threat hunting takes time and resources that many organizations simply do not have in-house. Check out WatchGuard report: the state-of-the-art threat hunting in businesses to know more about the challenges to adopting threat hunting in a business’s security program.
Managed security service providers enable a wide array of proactive security capabilities, including alert monitoring, prioritization, investigation, and threat hunting. They use sophisticated endpoint and network detection and response solutions, applying artificial intelligence models to correlate and prioritize advanced threats.
Keep in mind, these services are complex, requiring skilled personnel, technologies, and processes, and are not always cost-effective for security service providers.
Pulse and WatchGuard surveyed 100 information security leaders at managed security service providers (MSSPs) to find out how organizations mitigate this complexity to provide cost-effective managed threat hunting services to their customers.
State-of-the-art threat hunting in managed service providers
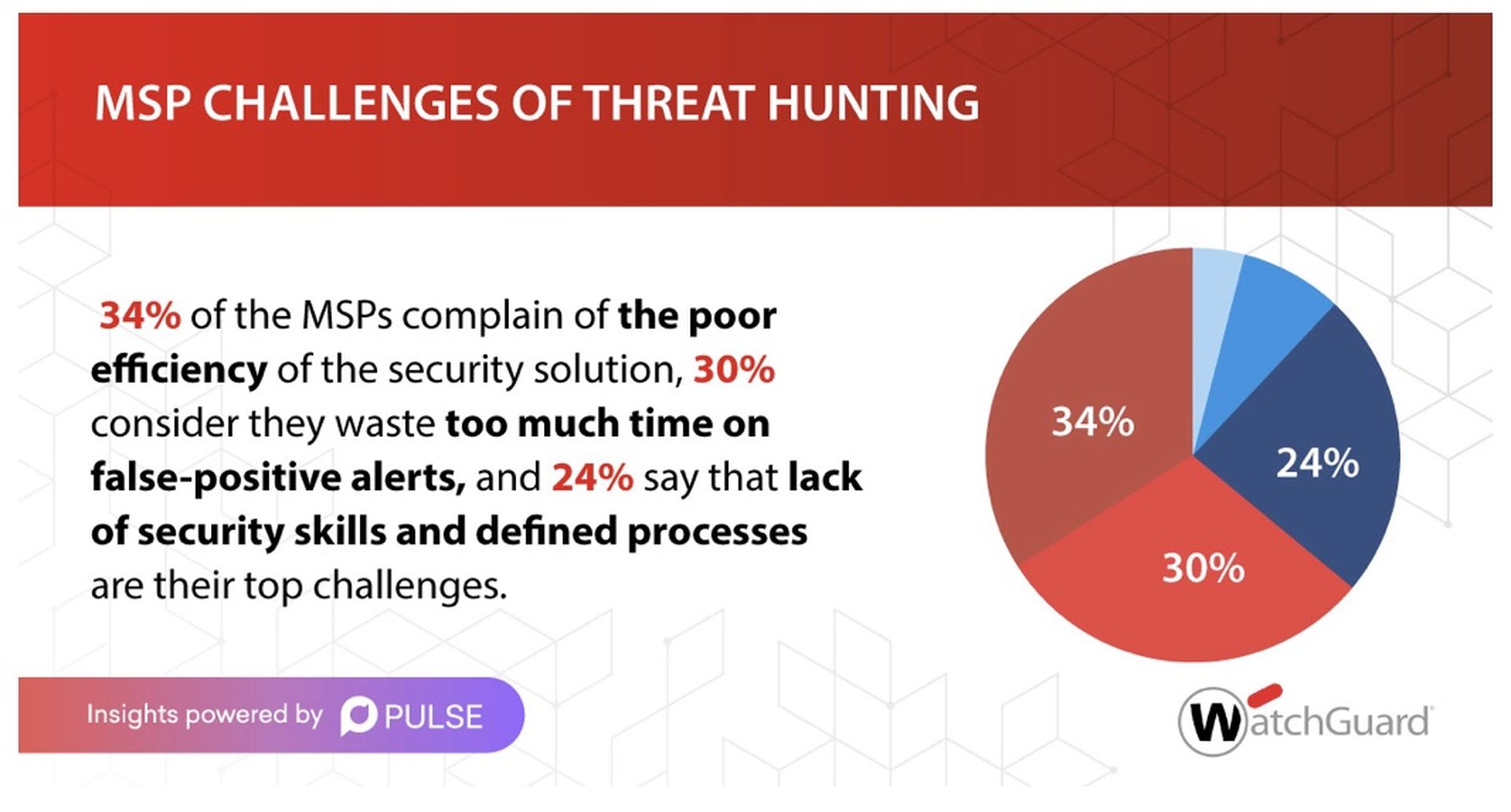
1. MSP CHALLENGES IN THREAT HUNTING
There are three main challenges they have to face: Poor efficiency of the security solutions that make them waste too much time in false-positive alerts, and the lack of security skills and processes to efficiently hunt, detect, prioritize, investigate, and respond.
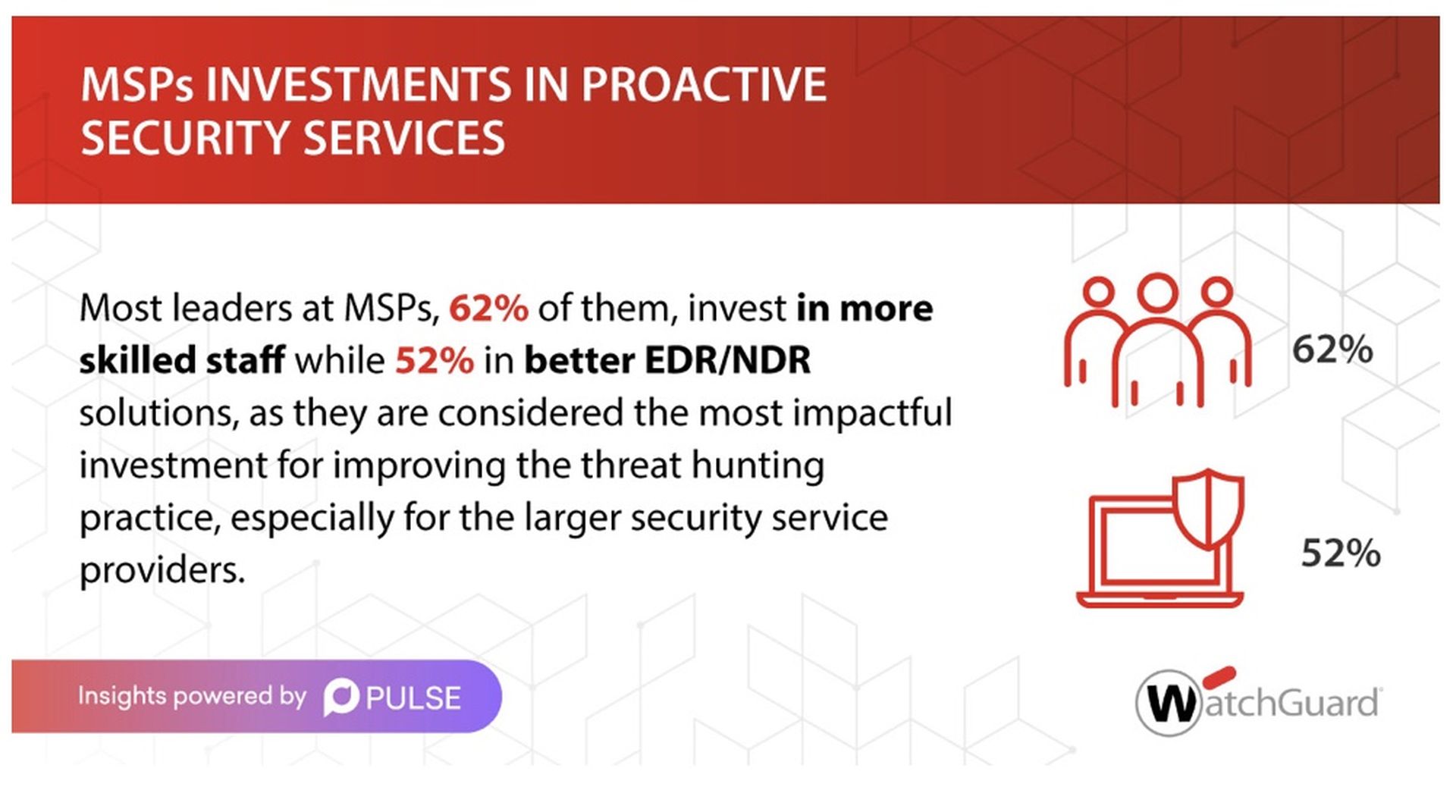
2. MSPs INVESTMENTS IN PROACTIVE SECURITY SERVICES
Most leaders at MSPs, 62% of them, invest in more skilled staff while 52% in better EDR/NDR solutions. They are considered the most impactful investment for improving the threat hunting practice, especially for larger security service providers.
3. MSP THREAT HUNTING MATURITY LEVEL
46% of MSPs provide proactive threat hunting services to detect unknown threats that have bypassed security controls. 55% of responders consider their threat hunting practices mature or very mature.


4. MOST THREAT HUNTING APPROACHES RELY ON EDR
73% of the MSPs use EDR solutions as part of their threat hunting approach and 55% NDR solutions. 45% consider endpoint activity the most valuable data source when hunting and investigating incidents.
The WatchGuard report: the state-of-the-art threat hunting in MSPs provides an in-depth analysis of MSPs’ adoption, challenges, and maturity level of MSPs when providing threat hunting service to their customers.
Adding threat hunting to your existing security program becomes crucial for shifting from reactive to proactive defense against ever-evolving threats. This shift is possible by combining endpoint protection (EPP) and detection and response (EDR) capabilities with Zero-Trust Application Service and Threat Hunting Service. It helps MSPs efficiently provide automated prevention, detection, and response with a proactive end-to-end threat hunting service.
The biggest benefits are that threat hunters and analysts continuously monitor everything that happens in real time and retrospectively in all customer telemetry. Continuous monitoring, cutting-edge technologies, such as security analytics and machine learning, and human-led proactive hunting services enable the discovery of hackers and malicious employees, leveraging increasingly sophisticated malware, ransomware, fileless malware and living-off-the-land techniques, and other advanced evasion threats.
Learn more by reading our latest eBook: Are you ready to take your managed security service to the next level?
Author Iratxe Vázquez is senior technical product marketing manager at WatchGuard Technologies. Read more WatchGuard guest blogs here. Regularly contributed guest blogs are part of ChannelE2E’s sponsorship program.




