The lure of digital is significant and brings rapid customer scaling, reduced operational costs and revenue growth. Strategies and transformations are abound, however so are the stories for security breaches, hacks and cyber threats. Digital does open up new threats, but why is the nature and the magnitude of breaches increasing? Why are companies regularly leaving the front door open? The answer lies in our (in)ability to understand risks from first principles.
Digital impacts the operating model, people, processes and technology, so a robust approach to manage risks of change is required. A crucial first step is a digital risk assessment that allows for an eyes wide open approach.
Threat, what threat?
A risk assessment serves to identify the key threats, vulnerabilities and proposed mitigation (controls) for digital change. Understanding this upfront allows relevant mitigations and controls to be embedded into operating models, processes and technology architecture to counter digital threats.
Table 1 (below) illustrates how key features of a risk assessment should be populated, from left to right to classify threats to ultimately identify mitigations and controls.
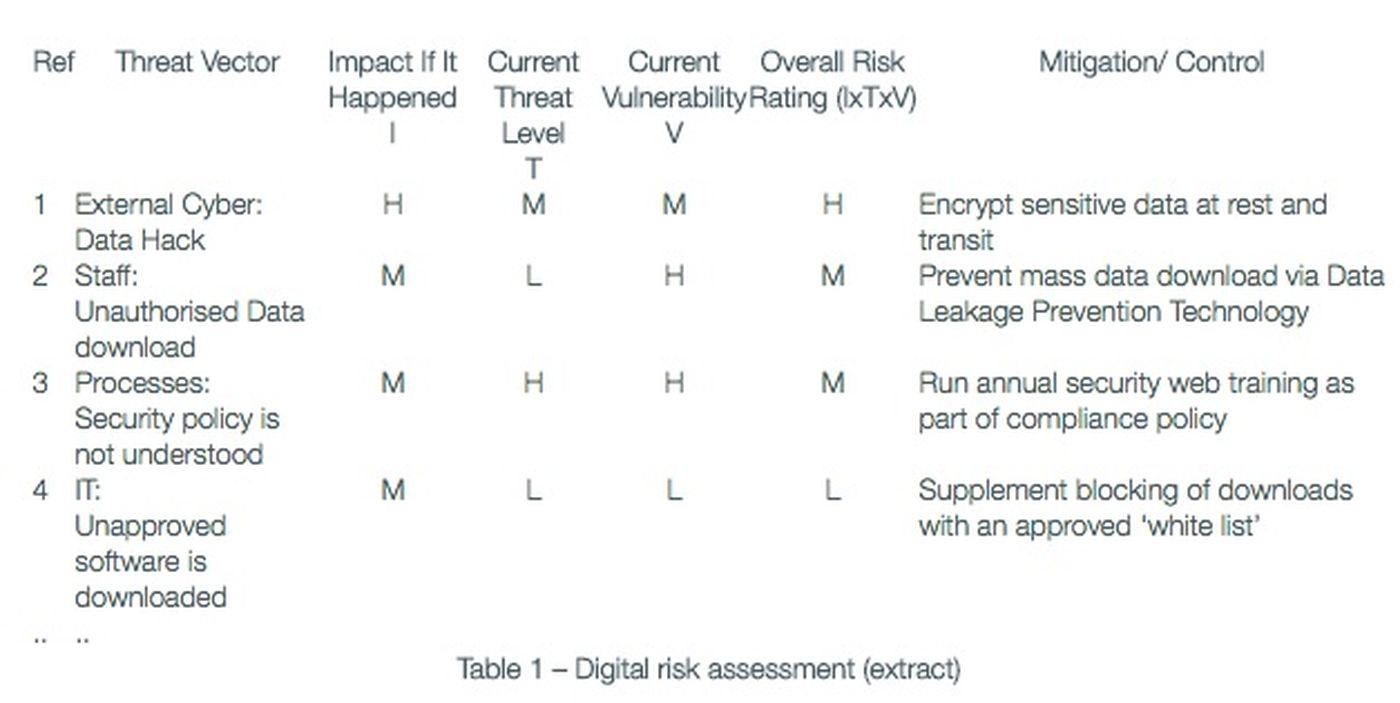
Numerous threat vectors can exist and for each one the ratings are provided based on the organization’s risk appetite. For example impact can include quantified thresholds for financial, reputational, health and regulatory areas. Similarly, threat and vulnerability ratings can be grounded in probability ranges. An overall risk rating then serves to prioritize risks for urgent mitigation through allocation of company resources or budget.
Although external (cyber) threat vectors capture the headlines, a key threat can be internal and such lesser perceived threats may actually present high overall risk ratings for action. The advantage of a structured risk assessment is that all relevant threats are considered and rated.
Control freak
So we now have a prioritized risk to be mitigated and controlled. How do we define a suitable control to mitigate a given risk? Controls can be classified as preventative/ detective and manual/ automated as below.

Fig 1 - Controls classification matrix
Preventative and automated controls are favored. We can illustrate this through the example of driving a car. Would you prefer to have a low fuel warning light in your car (preventative-automated control), or just notice that you have no fuel when you grind to a sudden halt (manual-detective control)? In practice, each threat will dictate the best type of control needed.
Doubly effective
Having identified the type of control required, the next step is to ensure that the control will be effective on two levels.
- Design effectiveness – the control will effectively mitigate the specific digital threat and risk
- Operating effectiveness – the control will always be effectively operating or in place
This can be extended to the car analogy. If the fuel sensor light activates only when there is 10ml of fuel remaining, then it is not an effective design, as you do not have enough fuel to reach the next fuel station. Similarly, if the fuel sensor itself has an intermittent fault, then the control is not operating effectively, as you will choose to ignore it.
You now have your risk assessment, control types and control effectiveness. The last step is implementation of controls as part of a digital or risk project. However, digital risk management is not a one off exercise, rather an ongoing activity cycle of assess, address, assure and repeat. The starting point should be an effective and comprehensive digital risk assessment.
Damage limitation exercise
Plan for the worst, but hope for the best. Despite effective risk management, new or old threats can still materialize. The ability to effectively respond to a digital incident can drastically reduce the impact for companies, thereby minimizing damage. To do so, the following strategies should be defined, practiced and be ‘good to go’:
- Incident management processes
- Regulatory notifications
- Public and shareholder relations
- Regular threat testing and updating of threat vectors
So, we leave the front door open because we don’t understand risks or how to treat them from first principles.
Now that you do understand, go and check whether your front door is open or closed.
To find out more, contact me at [email protected] or leave a comment.
Subhinder Dhillon is digital transformation director for financial services at Capgemini. Read more Capgemini blogs here.




