When it comes to battling endpoint security threats, MSPs would be forgiven if they found themselves constantly muttering, “And now what?” Protecting clients has become significantly more challenging as cybercriminals continue to find innovative new methods to outsmart conventional antivirus solutions.
For several years, the most alarming trend in malware and potentially unwanted application (PUA) executables has been polymorphism. Polymorphic malware and PUAs (such as spyware and adware) are generated by attackers in ways that make each instance unique. The reason the bad guys prefer this method is simple; it defeats traditional security approaches, which rely on the relative ease of detecting one instance of malware delivered to a large number of people.
By stark contrast, detecting a million unique instances of malware as they are delivered to the same number of people—and identifying that malware quickly enough to prevent a breach—is vastly more difficult, and requires a completely new approach to analyzing executables. That’s exactly what Webroot employs.
When Webroot SecureAnywhere® protection is installed on your customers’ endpoints, it creates a digital fingerprint of every executable file it encounters. That entails a multitude of unique digital fingerprints; during 2016, approximately 94% of the malware and PUA executables observed by Webroot were only seen once, demonstrating how prevalent polymorphism is.
Statistics such as these come from the threat intelligence metrics that are automatically captured and analyzed by the Webroot® Threat Intelligence Platform, an advanced cloud-based machine learning architecture that continuously produces the threat intelligence used by Webroot SecureAnywhere endpoint security products.
The Webroot threat intelligence and discovery model, along with its use of digital fingerprints from real-world files, was developed specifically to identify and stop polymorphic malware and PUA executables before they can damage their targets. Webroot endpoints observe hundreds of millions of new instances of executable files each year. Of the new executable file instances in 2016, approximately 2.5% were malware and 2.2% were PUAs.
As Figure 1 shows, there have been major changes in the relative percentages of malicious executables out of all new executables over the past three years:
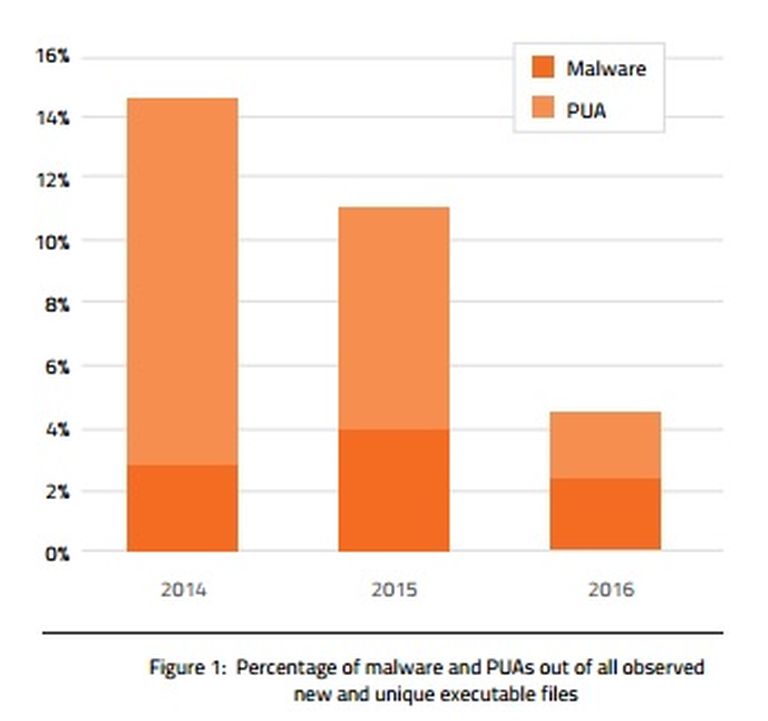
Malware’s share has dropped by 23%, while PUA’s share has plummeted almost 81%. More detailed analysis of the 2016 data reveals that the monthly counts of new PUAs fell throughout 2016; the volume in December was less than 20% of January’s volume.
There are two likely reasons that the volume of new malware and PUAs has stopped growing at the astronomical rates we had seen so far. First, during those years of incredible growth, attackers were changing from traditional malware and PUA creation to more automated, polymorphic file creation techniques, thereby creating many unique executables—rather than a single executable that could be blocked quickly due to its popularity. Once most attackers had switched to polymorphic techniques, the rate of growth abated.
Second, Webroot has enhanced its techniques for detecting malicious activity earlier in the kill chain, such as blocking executable files from being transferred to endpoints via malicious URLs, and preventing malicious executable files on an endpoint from downloading additional malicious executables. Because Webroot is more effective at preventing additional executables from reaching endpoints, those executables are no longer included in the observed files.
Although the decline in the volume of new malware reaching Webroot customers is certainly a positive trend, MSPs must continue to treat malware as a serious threat; approximately one in every 40 new executable file instances observed in 2016 was malware. These files are highly customized, often to target individuals, and they cannot be stopped by traditional malware detection technologies.
To learn more about polymorphism and Webroot’s innovative technologies to combat it, download your free copy of the 2017 Webroot Threat Report here.




