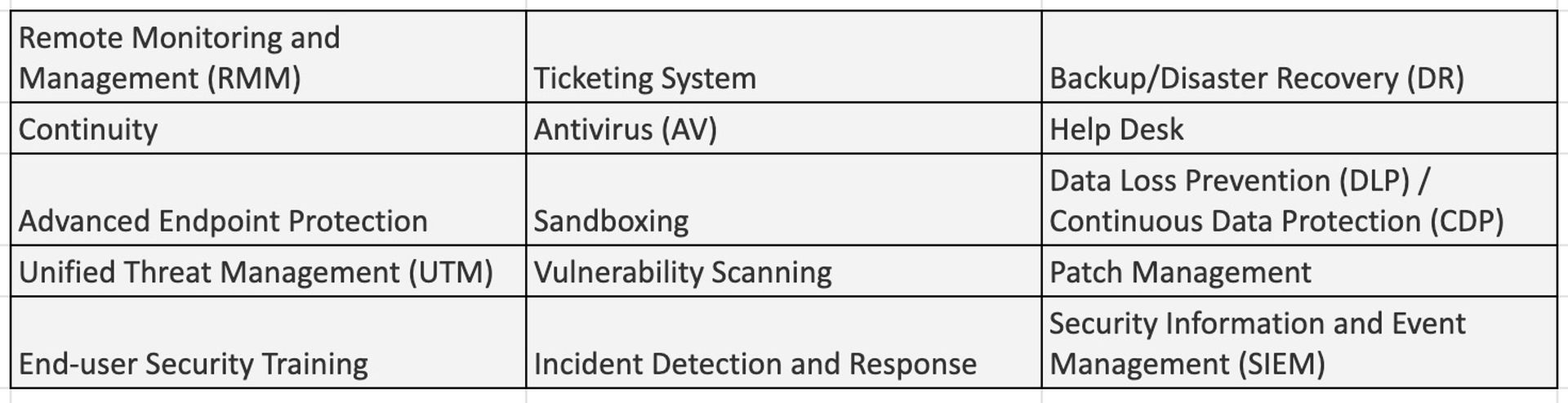
Here’s a question. How many tools does it take to secure a network? When you add everything up, a comprehensive approach requires a minimum of 15 different MSP tools:
New requirements for the MSP stack
 Author: Amy Luby, chief channel evangelist, Acronis
Author: Amy Luby, chief channel evangelist, AcronisYesterday’s managed services provider (MSP) had a typical stack at the core of their managed services offering. The main goal was uptime and reliability. This stack consisted of RMM, professional services automation (PSA), AV, backup and DR, network operations center (NOC), and help desk. Some MSPs now include a managed security services provider (MSSP) stack that consists of eight to 10 more solutions – including advanced endpoint protection, advanced email filtering, DLP/CDP, vulnerability scanning, SIEM, incident response and remediation, and security awareness training for the end-user.
For an MSP, that means 10 to 20 different vendors, software, and dashboards to manage, none of which are designed to work together. MSPs have to train their techs, manage their vendors, and just hope that nothing falls through the cracks that would put their clients at risk.
Many in the channel simply aren’t experts in the MSSP stack ... and that’s ok. We can’t be experts in everything. But how does a modern MSP deliver security and protection when they are the only things that matter?
What MSPs should consider
The conversation is shifting away from “Which tool is better?” to “What is the best way for me to safeguard client data?” We can agree that the only real MSP deliverable today is the outcome – protection. To deliver effective protection in today’s environment, we must implement modern processes and tools that ensure comprehensive security. And the research backs up that opinion.
That means today’s MSPs would be making a mistake to sell the stack mentioned above. Instead, they should be selling the protection outcome – the idea that, for a monthly fee, they’ll help keep the client’s business running because they’ve got the Five Vectors of Cyber Protection covered. Those vectors are:
- Safety: ensuring that reliable copies of data, applications, and systems are always available
- Accessibility: making data, applications, and systems easily available from anywhere at any time
- Privacy: controlling who has visibility and access to all of the client’s digital assets
- Authenticity: creating undeniable, certifiable proof that a copy is an exact replica of the original
- Security: protecting data, applications, and systems against today’s ever-changing cyberthreats
That approach is behind all of Acronis’ solutions. And while we can agree that there is no silver bullet when it comes to protecting data – no one tool will give us 100% protection at all times – this approach to cyber protection has Acronis coming pretty close to perfect.
Cyber protection designed for MSPs
Acronis Cyber Protect Cloud is a comprehensive protection solution that covers you from end-to-end. With Acronis Cyber Protect Cloud, you get a unique integration of backup and recovery, real-time antimalware protection, and endpoint management. It creates regular, reliable backups automatically and securely stores them so they’re available wherever and whenever.
The integrated design is aimed at helping both MSPs and their clients win. For businesses, Acronis Cyber Protect Cloud improves downtime prevention and accelerates remediation. For service providers, it enhances their security offering and eliminates the complexity of using multiple solutions. As a result, they can expect improved profitability, easier SLA compliance, and greater cost control.
MSPs that already offer Acronis appreciate the platform’s easy integrations with RMM/PSA tools, efficient consumption-based billing, comprehensive white labeling, and seamless scalability to deliver the outcomes their clients demand – complete cyber protection.
Amy Luby is chief channel evangelist at Acronis. Read more guest blogs from Acronis here.




