Gartner Peer Insights and Cisco surveyed 100 network, IT, and security experts who evaluate or purchase cybersecurity and identity management tools to understand what they value and prioritize in today’s evolving threat landscape. One trend from this survey is clear: Hybrid work is here to stay. That means security leaders must continue to find better ways to secure access to corporate resources, without stopping employees from doing their jobs.
So, what can we learn from these survey results? Here are the 3 key challenges that security experts must navigate:
1. Managing a larger attack surface
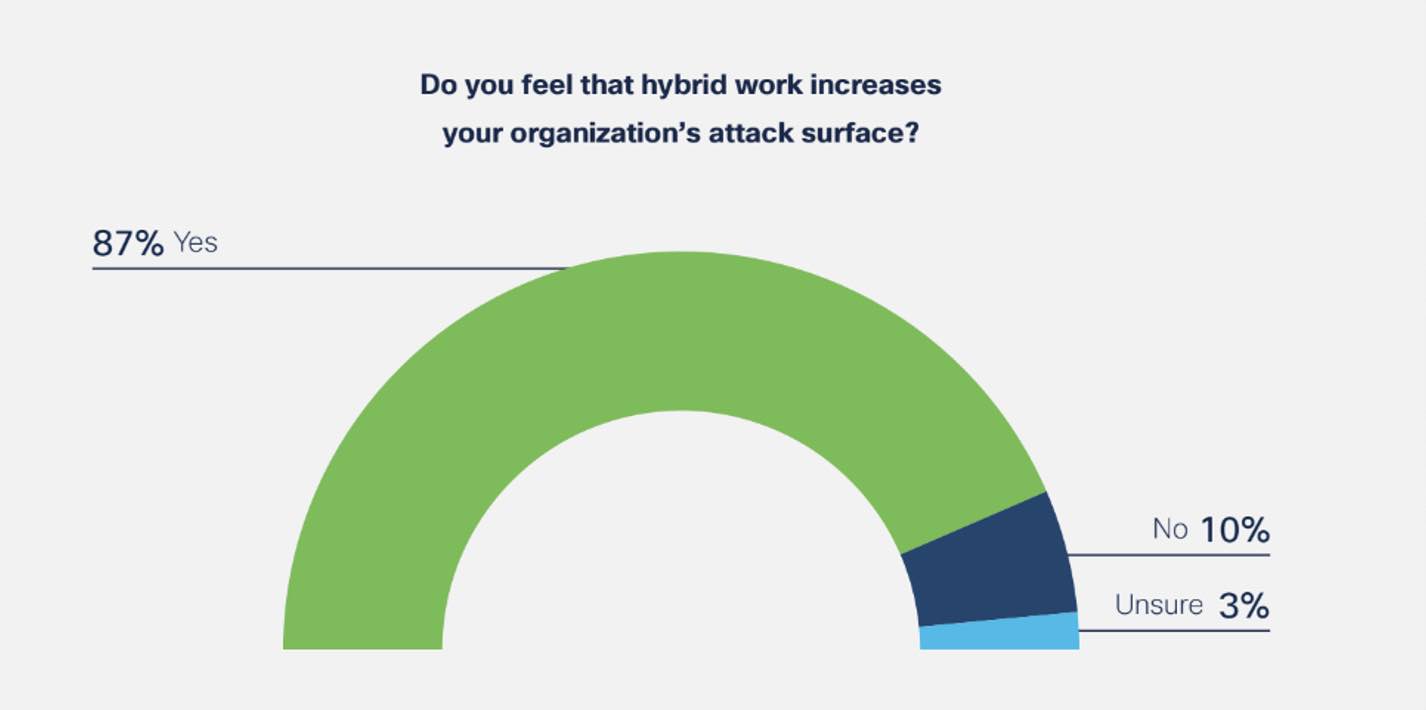
Hybrid work means that employees are still logging in from the corporate network, but they are also logging in at home, on various devices, and changing locations. When companies had to manage one corporate device in one location, it was easier to differentiate between risky and normal user behavior. However, as the attack surface has increased, and the number of potential risk signals has increased, it makes it difficult for security teams to manage these new risks.
One approach companies can take to improve their security posture is to put controls in place to prevent bad actors from gaining access. This includes using multi-factor authentication to protect user accounts, using device trust policies to assess device health and control access across managed and unmanaged devices, and setting up remote access policies to protect applications, regardless of user location.
2. Balancing risk signals and privacy
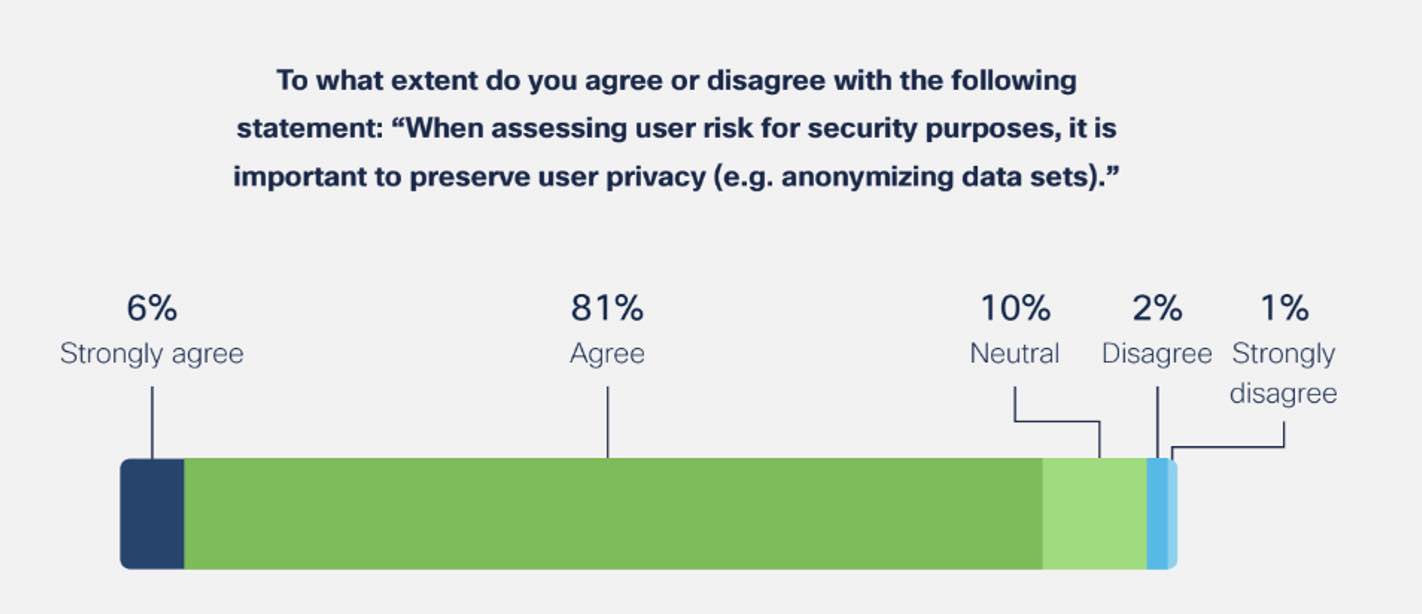
Organizations can evaluate risk in the environment by tracking contextual signals to determine if there is any anomalous activity. However, analyzing risky behavior can sometimes lead to violating individual’s privacy if those signals are too intrusive.
In Duo’s new Risk-Based Authentication solution, we have developed a new risk signal, called Wi-Fi Fingerprint, to evaluate changes in location without invading the user’s privacy. Wi-Fi Fingerprint evaluates location by turning the Wi-Fi network information into a new data point that also anonymizes the user location. Then, Duo can compare current and past Wi-Fi Fingerprint data points to determine risk-level, without ever knowing that specific user location to begin with.
3. Making it easy for trusted users
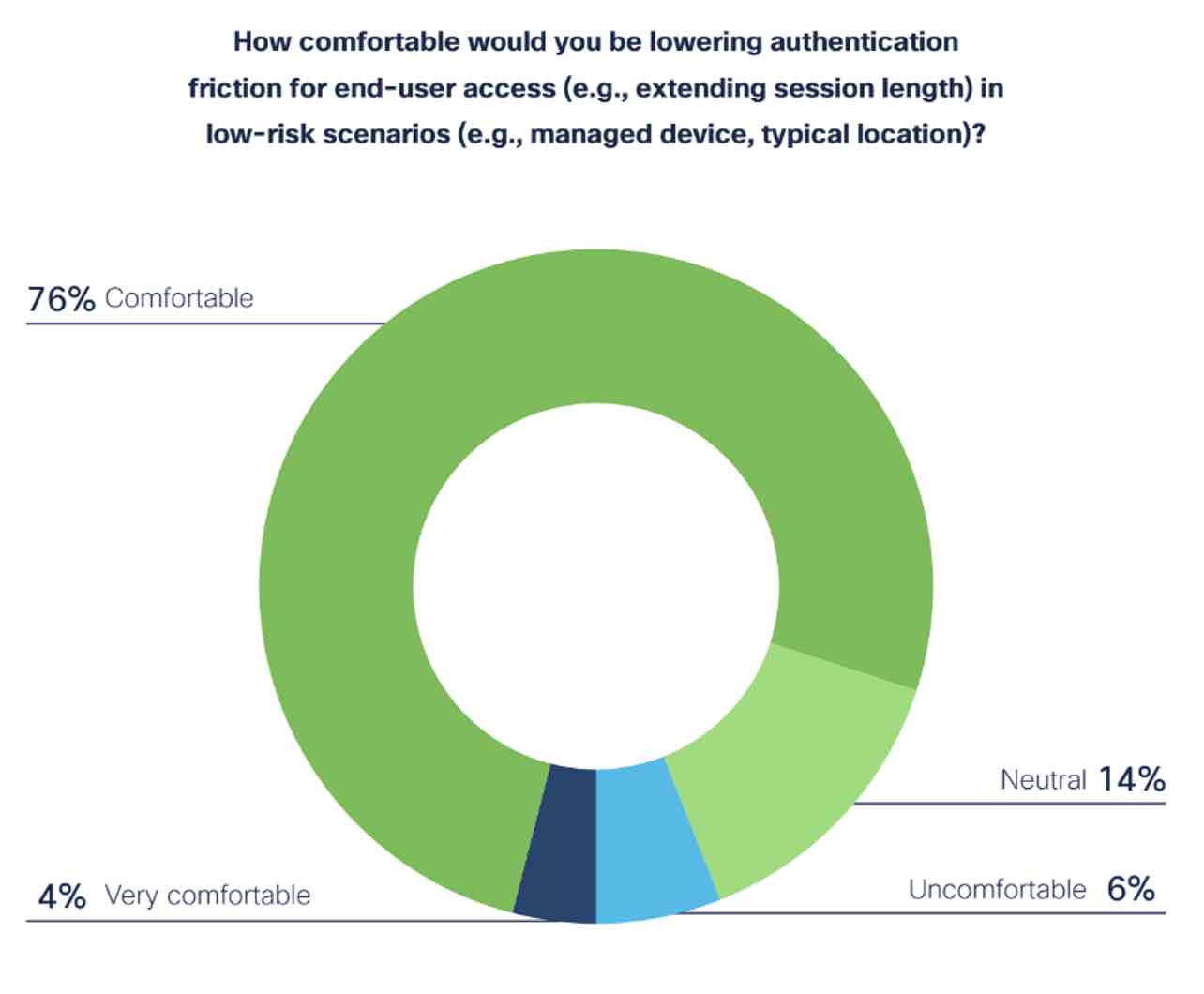
Ultimately, security teams want to make it difficult for bad actors to gain access, but don’t want to get in the way of trusted users doing their jobs. However, if a company cannot differentiate between a low and high-risk scenario, then they cannot make it easier for trusted users to login. Duo’s new Risk-Based Remembered Devices policy allows users to automatically gain access to corporate resources when risk is low, and revoke that trust and require re-authentication if there is a change in behavior.
This allows security teams to feel confident about allowing their users to have longer sessions, and authenticate less frequently, without sacrificing security.
Want to learn more about securing hybrid work?
It is clear that the nature of work is rapidly changing. Security teams face a variety of new challenges as they seek to defend a larger attack surface against an evolving threat landscape. Duo is here to partner with organizations to help them achieve their security goals, without preventing trusted users from doing their job.
To learn more, check out the Gartner Peer Insights Survey Results.
Guest blog courtesy of Cisco Systems.




