
Identity and Access Management (IAM) is a very important functional area of cybersecurity, as it involves identifying the people, accounts, and objects connecting to your network and accessing your data, applications, and other resources. These capabilities are critically important to the protection of the modern enterprise, where billions of computers are communicating together over the internet, every day, serving the purposes of billions of people conducting their personal and business lives. The old joke, “on the internet, nobody knows you’re a dog,” holds true and is applicable as ever.
Failures in IAM can result in inadvertent breaches of data, intruder access to online systems, and loss of control of enterprise IT. Many of the most devastating cyberattacks of the past two decades have involved some measure of IAM breach, compromise, hijacking, or failure.
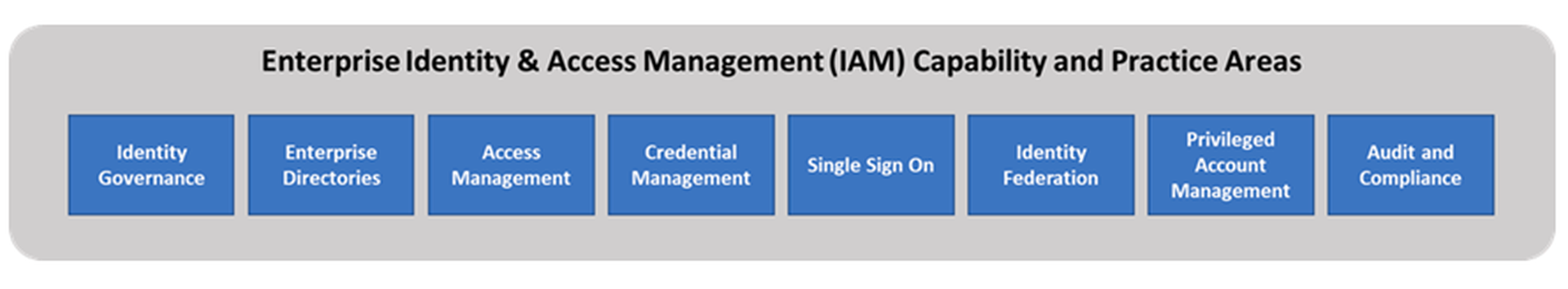
Eight IAM Capabilities
As a security practice, IAM usually involves eight major areas of capabilities, processes, and technology:
- Identity governance: The process of managing the lifecycle of electronic identities, including identity provisioning, de-provisioning, and revision upon changes to relationships, roles, permissions, and personnel
- Enterprise directories: Infrastructure used to keep track of who the users are and what they can access, and to make that information available to enterprise IT applications
- Access management: The process of identifying who can access what and who can do what within the enterprise, its data, and its applications; major access management models role-based access control (RBAC) and attribute-based access control (ABAC)
- Credential management: Capabilities related to managing user credentials including password policies, password management, password reset, account unlock, and emergency access; also includes management of biometric identity validation, multi-actor authentication (MFA), and cryptographic keys used for online identities
- Single sign-on (SSO): Capabilities related to enabling enterprise users to access multiple applications without having to log in separately to each application; this greatly simplifies the user experience and productivity
- Identity Federation: Capabilities related to allowing the organization to conduct identity collaboration, or federation, with external parties; with federation, the organization can allow third parties to validate their users’ credentials when those individuals access the organization’s IT systems, and can similarly allow its users to access third-party applications, without having to directly share credentials
- Privileged account management (PAM): Capabilities related to managing highly privileged accounts such as system administrator accounts, application administrator accounts, system and service accounts, and “break-glass” emergency accounts or system backdoors; usually coordinated with network protections, bastion hosts, and MFA capabilities to provide robust protection for system administration channels
- Audit and compliance: Capabilities related to tracking user logins, permissions, and activity, to detect cyber incidents, investigating cyber incidents, and auditing cyber controls related to IAM.
IAM Becomes Critical
Over the past decade, IAM has dramatically increased in importance for most enterprises. Several factors drive this increase:
- First, breaches targeting user accounts and credentials have caused the enterprise to pay increasing attention to their users, their users’ accesses, and the protection of their accounts.
- Second, the transition to cloud computing has broken down the traditional network perimeter and replaced it with an enterprise IT ecosystem, protected not by firewalls but by user credentials.
- Third, the increased use of third-party contractors, third-party services, and external providers has made it increasingly difficult to keep track of who has access to enterprise data, when, and why.
- Fourth, increased security regulation, scrutiny, and liability have resulted in an increasing number of regulators, auditors, and insurers taking interest in the organization’s online identities and their accesses.
Over the past several years, we have seen these drivers cause many of our clients and partners to invest significantly in deploying, maintaining, expanding, and improving their enterprise’s IAM capabilities. A strong IAM infrastructure can help the organization effectively apply its policies and standards to reduce cyber risk across the enterprise and supply chain, and ensure the ongoing compliance of its cyber program.
Author Chris Williams is chief security officer and strategy lead at Capgemini. Read more from Capgemini here.




